Modernizing Data Security is Key to Successful Enterprises
The Problem
In 2022, the US Inspector General (IG) has found that the Department of Homeland Security (DHS) OIG Rates DHS Information Security Program ‘Not Effective’ – HS Today, the USPS IG Warns about State of USPS Cybersecurity (fedweek.com), the IRS IRS cyber deficiencies leave taxpayer data at risk, IG report says – FedScoop, DOD contractors deficient in cybersecurity defenses Defense R&D contractors inadequate in protecting sensitive data, IG says – FedScoop. There were more. The Security Exchange Commission (SEC) announced cybersecurity deficiencies SEC.gov | SEC Announces Three Actions Charging Deficient Cybersecurity Procedures
A Theme of Outdated Methods
The common theme from all these IG, GAO and SEC reports are organizations utilizing outdated methods that rely on analog systems that are difficult to verify by a technician and monitor at the manager’s level. Even the SEC SOC-2 system for financial institutions and the DOD NIST 800-171 framework for defense contractors repeatedly allow for vulnerabilities that permit non-compliant, non-certified and untrained vendors.
Six Critical Steps to Modernize Data Security
Forbes article is an easy to understand list of Six Critical Steps to Modernize Data Security (forbes.com)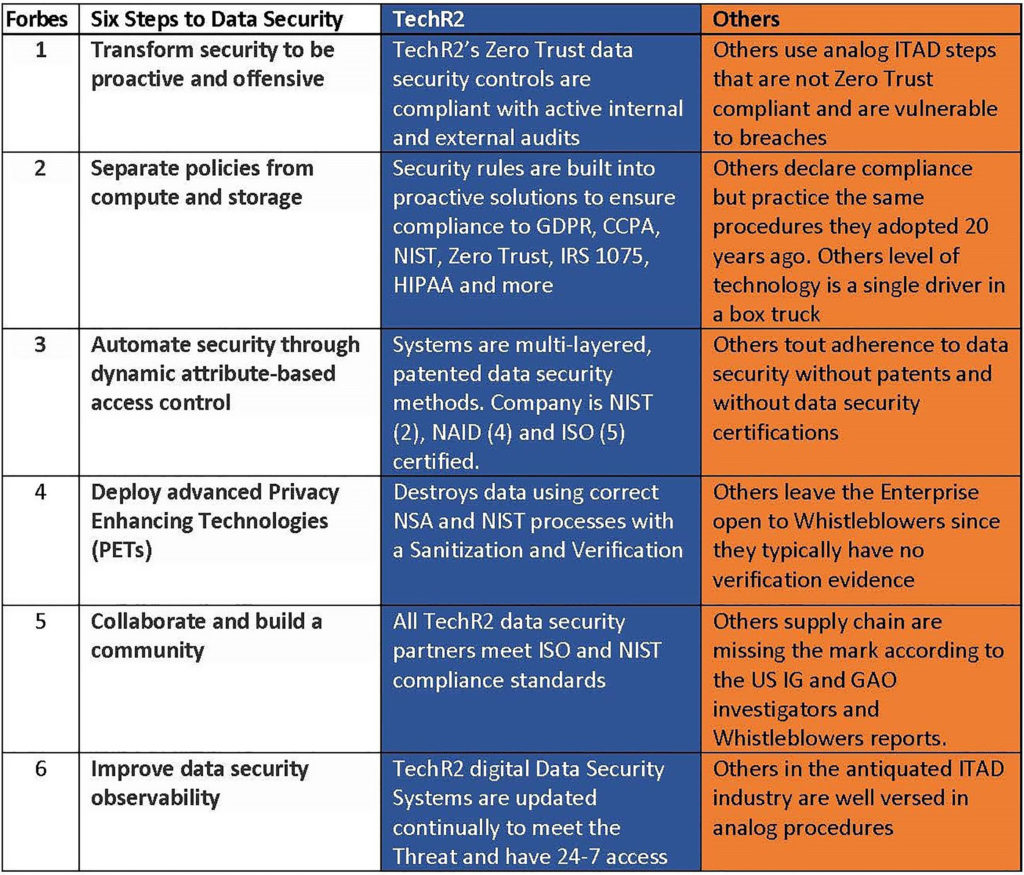
The Solution
Patented Tear-A-Byte® Method is the Future of EoL Solutions (Patented Tear-A-Byte)
Your answer to your cybersecurity control challenge is the ISO, and NIST certified TechR2’s Patented Tear-A-Byte solution. Patented Tear-A-Byte Method is the Future EoL Solution All TechR2 products and services incorporate Zero Trust Architecture data security techniques. Zero Trust Model
Data Security is Our #1 Priority (Data Security #1)
Resting on TechR2 industry and data security foundational certifications is training and engineering innovation to conduct efficient datacenter and enterprise decommissioning and refresh. Customer surveys from OEMs and Fortune companies mark TechR2 as excellent in all areas where in national IG and GAO reports other data destruction companies are scored as failing. Data Security is Our #1 Priority
Private Enterprise and Government Entities will not Miss the Regulatory Tsunami (Regulatory Tsunami)
FISMA Federal Information Security Modernization Act | CISA, IRS 1075 Publication 1075 (irs.gov), CJIS Security Policy CJIS Security Policy, CMS Information Systems Security and Privacy Policy CMS Information Systems Security and Privacy Policy and more all map directly to required NIST Cybersecurity Controls. TechR2 fully meets these standards while other companies do not.
Contact TechR2
TechR2’s NEW Data Destruction as a Service (DDaaS) is the future model and the archaic ITAD processes are outdated. DDaaS Data Destruction as a Service – TechR2.
Contact Sepp Rajaie to learn more. Contact our experienced TechR2 staff.









