
Track > Contain > Destroy > Verify
Introducing Tear-A-Byte
The Most Secure and Compliant Solution Available
The patented Tear-A-Byte appliance and process exists for one reason: To fully protect you from data breaches related to mismanaged, failed, or retired drives in your datacenter.
Be Confident Your Data is Eradicated
And Tear-A-Byte is the only solution that meets these standards.

securely in a locked appliance, accessible by only certified staff, who will be automatically notified as your Tear-A-Byte approaches capacity.
on these hard drives within your four walls and receive a Certificate of Destruction before our team leaves that day.
via controlled teams and easily accessible electronic reporting to reconcile your IT asset inventories and ensure data security and prove compliance.
- Compliance is Our Obsession.
- Experience an Indisputable Chain of Custody
- Reexamine and Redefine Your ROI.
Compliance is Our Obsession
Experience an Indisputable Chain of Custody.
By containing drives in our secured Tear-A-Byte appliance and then eradicating the data on those drives within the four walls of your facility, you have the tightest chain of custody imaginable because the drives never leave your possession until data eradication is complete and confirmed.
Reexamine and Redefine Your ROI.
ROI
While most ITAD companies have convinced people to focus their ROI solely on recovered value, the true costs and savings of managing your end-of-life assets should include the measure of time.
self-audited
Our clients have self-audited their processes and reported time savings approaching 50 minutes per drive in processing and compliance time, when comparing the Tear-A-Byte process to their legacy methodology.
Reconciliation issues
That doesn’t even account for the time saved when clients no longer have to account for reconciliation issues thanks to their lost-device rates going from around 5% all the way down to to 0%.
And if you factor in avoiding 6- and possibly 7-figure fines for unaccounted data, the ROI of Tear-A-Byte is in fact quite astronomical.
Subscribe To Our Newsletter

Why Choose Us
Our Commitment to Innovation:
Why won’t we rest on our laurels? Because we know the cyber criminals out there aren’t resting either. We are fully committed to always providing you with the most secure, compliant, and easy-to use solutions related to destroying the data on your hard drives, laptops, smartphones, POS equipment, or any other piece of data-bearing IT equipment.
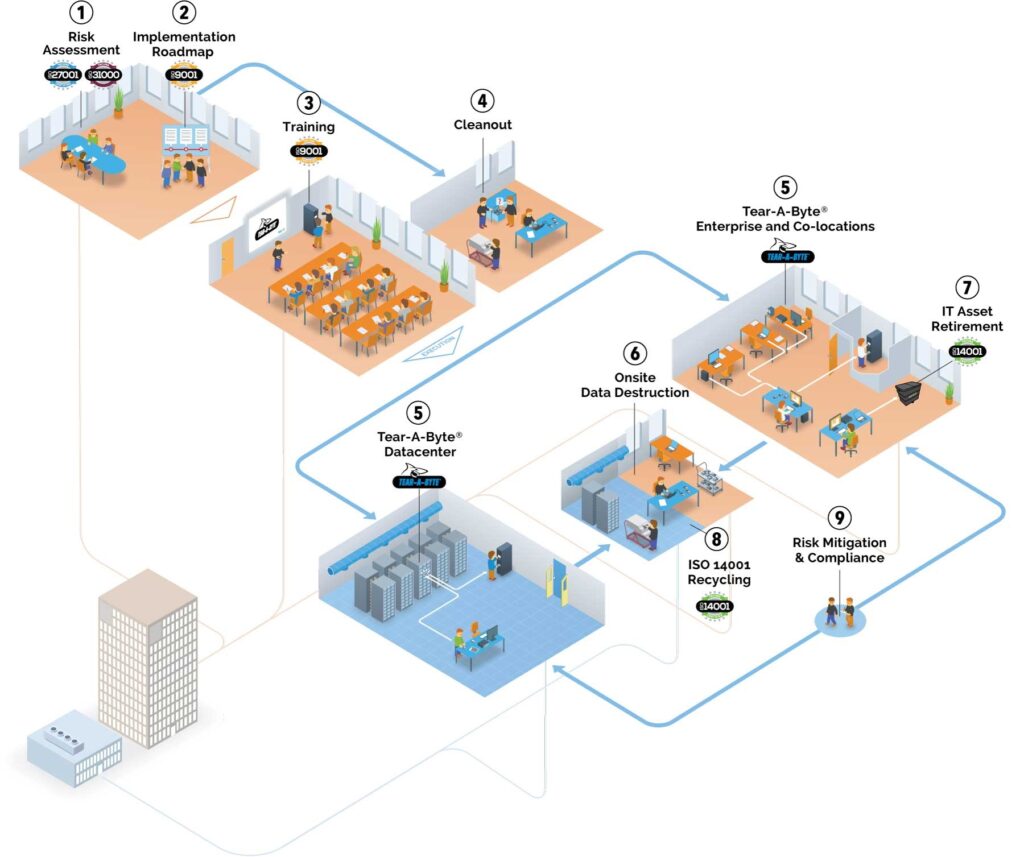

via photography, barcodes, and PID technology to establish a real-time inventory and audit trail; easily visible in your customized portal.