
Whether moving to the Cloud or not, data controls are always paramount!
If your enterprise has moved to the cloud or maintaining its own datacenter, your data protection continually remains essential. The ever-growing threats, both internal and external, begins precisely when media becomes removed. If it is not tracked, if it is not contained, if it is not properly destroyed under your control, or if it is not verified, then all of the proper data controls have not been established. Here are just a few data controls needed:
Enterprises must control all data in possession
US state, federal and industry regulations require you, the enterprise to remain in control of the PII, PHI and financial data on your endpoint devices. Arrow shut down its centralized processing site where it had client data in its possession. Other old modeled centralized ITAD processing plants have PII, PHI and financial data on their premises without the required legal agreements that give them control of the data.
Laptop and desktop endpoint devices are fine, but hard drives need to be destroyed and the remnants recycled to ISO 14001 or equal standards.
Company personnel are required to classify each endpoint device regarding the stored level of data per system. PII, PHI and financial data are good examples. For many in the professional or commercial business, data bearing components must be destroyed to NIST 800-88 requirements through NIST 800-53 or NIST 800-171 Cybersecurity Frameworks.
Overwrite
For other endpoint devices containing public data, devices can be overwritten to the NIST standard.
“Just as organizations enjoy automation benefits that datacenters offer, data breach perpetrators do also.”
The 4 perimeters.
“IBM estimates data loss from physical breaches due to unauthorized access at $400 billion annually.”
TechR2 deliniates and helps fortify 4 perimeters needed for the datacenter.
A 3rd Perimeter prevents the risks leading to unauthorized access to data, reported as:
Risk Two: The Outsider Threat
Risk Three: The Seemingly Innocent Personal Item
Risk Four: Insufficient or Nonexistent Identity Verification
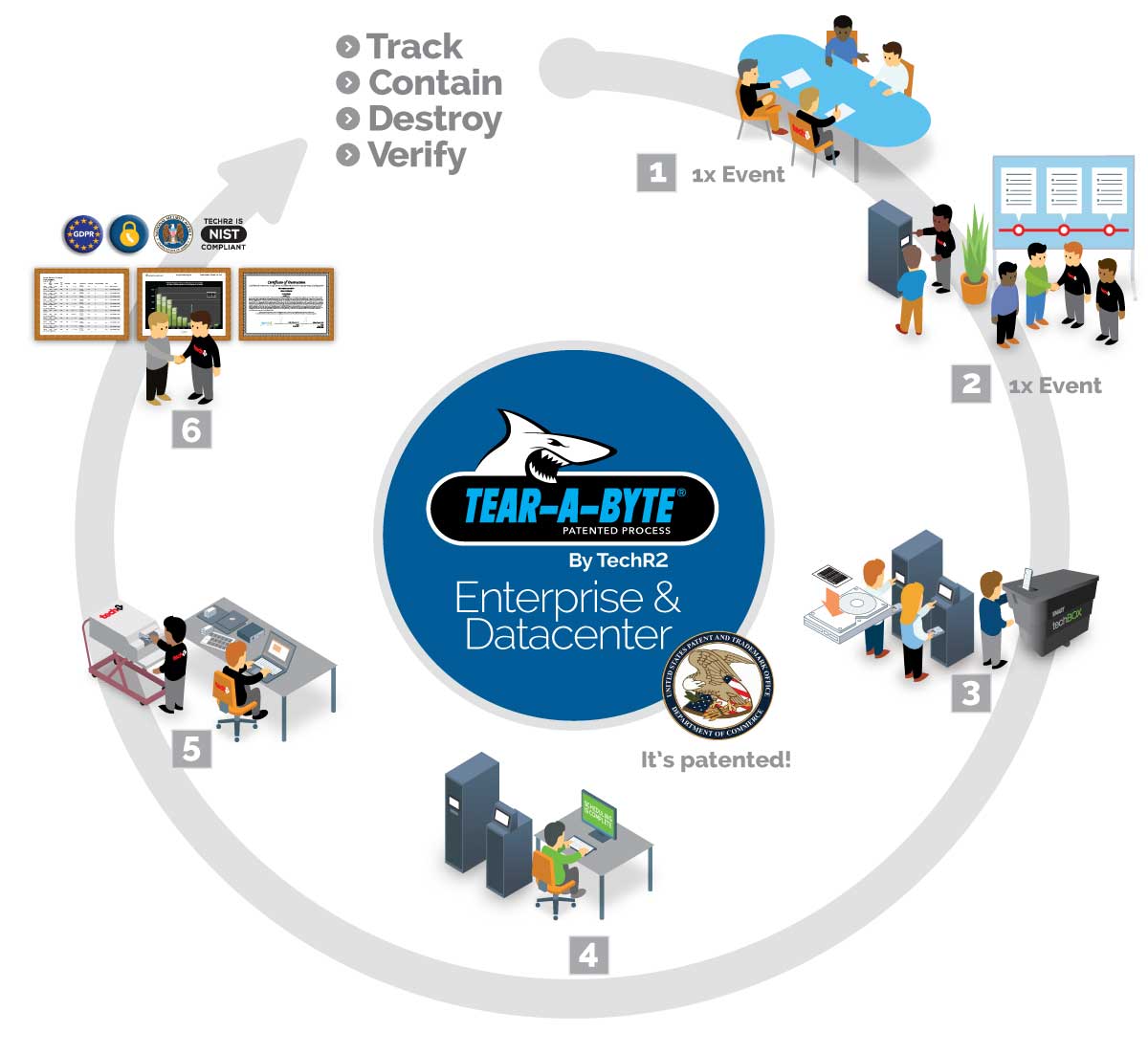
Peace of Mind in 6 Steps, by TechR2
Our DDaaS Process
Begins at Step 1
TechR2 performs a risk assessment to fully identify risk for data at rest and check compliance to industry and federal regulation. This is a single event.
A plan is created to secure the datacenter and all loose data bearing devices throughout the enterprise. Customer’s also go through a brief training session for using Tear-A-Byte®.
RFID tagging for each device establishes real-time tracking and inventory control. The secure Tear-A-Byte appliance receives and contains each device. For retired assets that do not contain critical data, the SMART techBOX offers containment-to-disposal management.
Once filled to capacity, a TechR2 field team is notified and dispatched via the proprietary TechR2 Customer Inventory Management portal. They will arrive onsite at a conveniently scheduled time.
TechR2 field teams verify and destroy all media onsite using NSA and DoD approved technology and processes after capturing, auditing, and reconciling the data bearing device. Security Engineers double verify the reconciliation process to ensure a successful process.
After approval of the onsite report, the client receives a Certificate of Destruction, Environmental Report and a detailed Audit Report via the TechR2 Customer Inventory Management portal.
Certification Matters.
Awarded a US Patent for our Track-Contain-Destroy-Verify process, we have the proprietary critical data management solution that’s effective for any enterprise. We are also OEM approved, we uphold six rigorous ISO certifications, including ISO 27001, ISO 14001, ISO 9001, and ISO 45001, and are recognized for compliance with GDPR, NIST and all governmental regulations concerning data destruction.

Solid DDaaS
Our field teams will make it happen!
Compliance to NIST SP 800-53, NIST SP 800-171, HITRUST, HIPPA, PCI, NERC, FERPA and other Cybersecurity requirements
Annual Risk Assessment at the Tear-A-Byte Site
Free IT Asset Recycling at the Tear-A-Byte site using TechR2 SMART techBOX Containers
Integrated Training at the Tear-A-Byte Site
Green Reports for Environmental Responsibility
Legal Certificate of Destruction (Sanitization)
Audit Reports 24/7 on the Customer Portal
Why risk it alone?
Get started today.
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Independent
- Competent
- Results-driven
- Problem-solving
- Transparent
What happens next?
Schedule a call at your convenience
We do a discovery and consulting meeting
We prepare a proposal





